Windows Defender detects Trojan:Script/Wacatac.B!ml in a zipped .NET 9 AOT binary
Posted by Dylan Beattie on 09 December 2024 • permalinkEarlier today, somebody alerted me that Rockstar binary releases for Windows were being blocked by Windows Defender… and sure enough, since I switched the build system from .NET 8 to .NET 9, the Windows ZIP file releases on the releases page are being incorrectly identified as being infected with Trojan:Script/Wacatac.B!ml malware.
It’s not just Rockstar, though. It’s any .NET 9 binary compiled with AOT enabled and then compressed in a ZIP file. Try it. First, create a new .NET 9 console app:
dotnet new console -o HelloWorld
Then edit the .csproj file and add StripSymbols and PublishAot directives:
<Project Sdk="Microsoft.NET.Sdk">
<PropertyGroup>
<OutputType>Exe</OutputType>
<TargetFramework>net9.0</TargetFramework>
<ImplicitUsings>enable</ImplicitUsings>
<Nullable>enable</Nullable>
</PropertyGroup>
<!-- ADD THIS PropertyGroup to create native binary EXE builds -->
<PropertyGroup Condition="'$(Configuration)'=='Release'">
<DebugSymbols>False</DebugSymbols>
<DebugType>None</DebugType>
<PublishAot>true</PublishAot>
<StripSymbols>true</StripSymbols>
</PropertyGroup>
</Project>
Now publish a binary release:
dotnet publish -c Release -o published
Look in /published and you’ll see a single binary HelloWorld.exe
Create a ZIP file containing that EXE - in Windows Explorer, right-click, Send to > Compressed (zipped) folder:
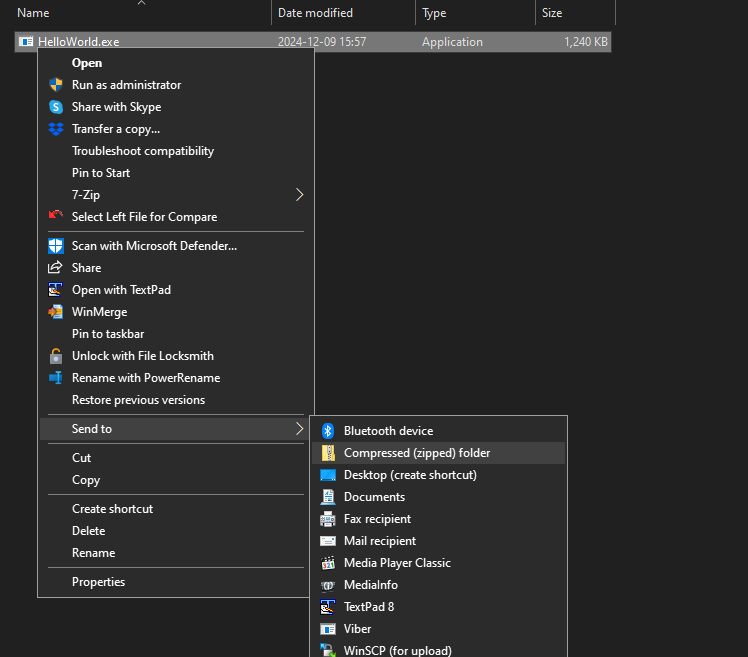
Right-click the ZIP file, Scan with Microsoft Defender…
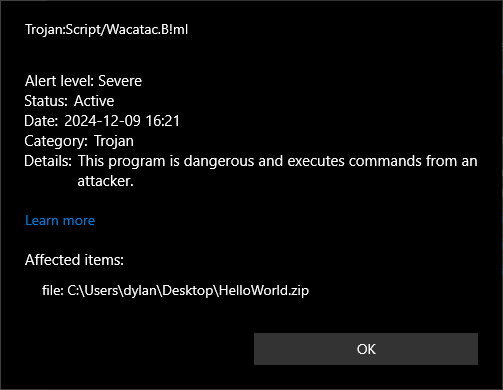
For a second opinion, upload the ZIP file to VirusTotal.com, and you’ll probably see that Microsoft Defender thinks it’s infected with a trojan. I’ve had multiple hits reporting Trojan:Script/Wacatac.B!ml and one reporting Trojan:Win32/AgentTesla!ml
